In Azure so far, we use NSG (Network Security Groups) or NVAs to filter network traffic. However, now we have the native Azure Firewall service for this purpose.
When it comes to network security, firewall defines the boundaries for your network infrastructure.
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It’s a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
Azure Firewall can be centrally created, managed and log application and network policies across subscriptions and virtual networks.
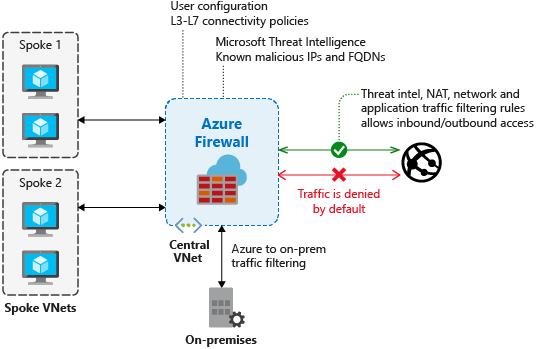
The above image illustrates how Azure Firewall can be deployed in a Hub and Spoke topology where all the Spoke Networks are peered to the Hub Network, and all the outgoing traffic are routed to the Azure Firewall in the Hub.
Features
- FQDN tags – Makes it easy to allow Azure service network through the Azure Firewall. E.g. Windows Update, Azure Backup.
- Application FQDN filtering rules – Limit outbound HTTP/s traffic to a list of fully qualified domain names including wildcard.
- Network traffic filtering rules – Allow/deny rules by source, destination IP, port and protocol.
- Threat intelligence – Alert or deny traffic to/from malicious IPs and domain. The IP addresses and domains sourced from the Microsoft Threat Intelligence feed.
- Azure Monitor logging
- Multiple public IP addresses – You can associate multiple public IP addresses (up to 100) with your firewall.
- Span multiple Availability Zones – To achieve high availability, it can be configured during deployment to span multiple Availability Zones.
Benefits
- Can be deployed in a Hybrid environment.
- You can use FQDN tags and FQDN for limiting HTTP/s traffic.
- You do not have to rely on a 3rd party solution (NVA) for firewall capabilities.
- You can log all the Network and Application Rule hits using Log Analytics Workspace.
- Threat intelligence-based filtering can be enabled to block traffic from malicious IPs and domains. The IP addresses and domains sourced from the Microsoft Threat Intelligence feed:
Use Cases
- Filtering inbound/outbound connections: Azure Firewall can be used to limit access to only specific FQDNs/IPs traffic.
- Hybrid Network: It can be used in a scenario where you have a multi-Network environment. You can use Azure Firewall to control network access in a hybrid network using rules that define allowed and denied network traffic.
- NAT Rules: NAT rule collection can be used to translate your firewall public IP and port to a private IP and port.
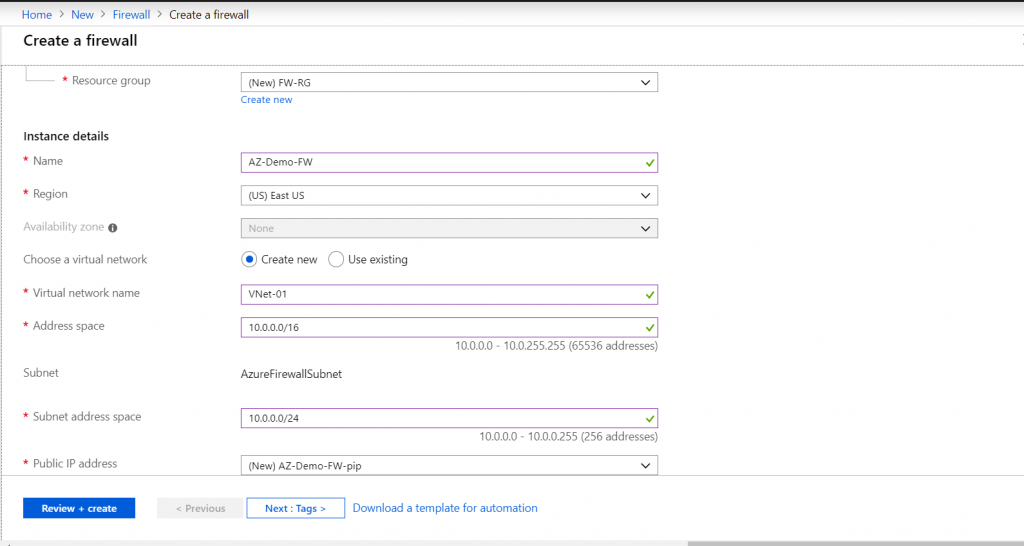
How to deploy Azure Firewall using Azure Portal:
Requirements
- Subnet Name must be AzureFirewallSubnet.
- Route table that must have a Route: Address prefix: 0.0.0.0/0, Next Hop Type: Set as “Virtual appliance” and the Next Hop address must be the private IP of the Firewall. Associate all the Subnets whose traffic has to go through the Firewall.
For more details on Azure Firewall visit Microsoft Docs.








