Please refer the below link for Azure Disk Encryption for IAAS Windows VM with Azure AD- Part 1
https://www.ifi.tech/azure-disk-encryption-for-iaas-windows-vm-with-azure-ad-part-1/
Create New Application in Azure Active Directory
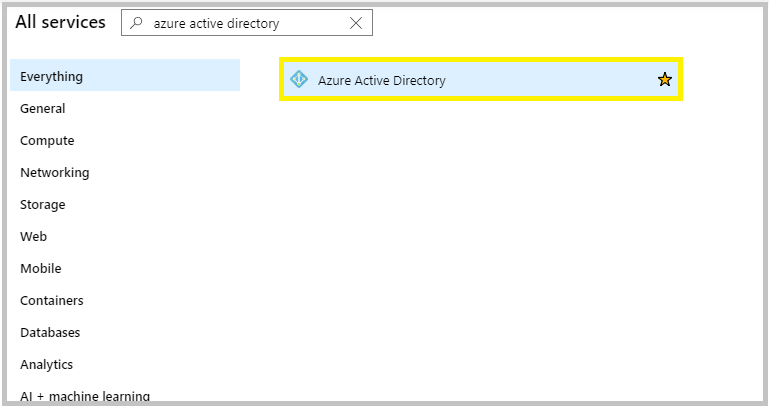
- In the portal, go to All Services and search for Azure Active Directory.
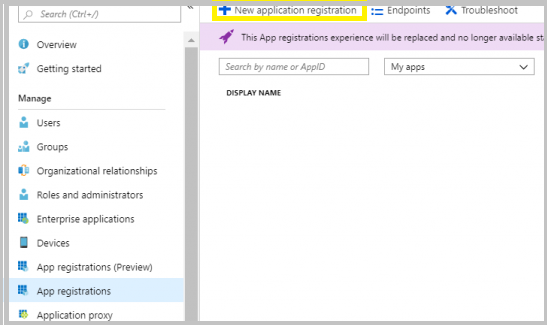
2. From the blade, choose App Registrations and click +New application registration.
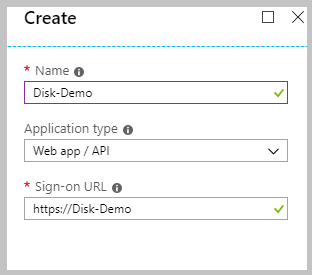
3. Provide a name and URL for the application.
Select Web app / API for the type of application you want to create.
You can’t create credentials for a Native application. You can’t use that type for an automated application. After setting the values, select Create.
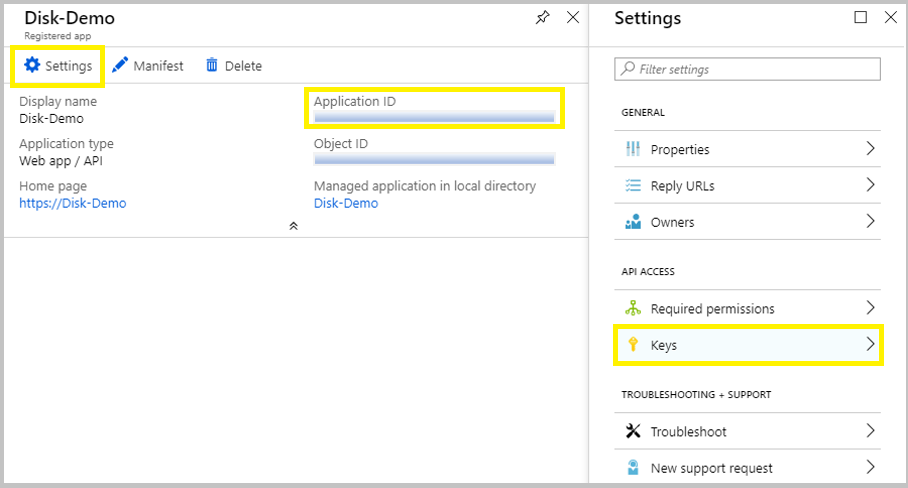
4. After the Application Registration is successfully created, go to the Application that was created and copy the Application ID as it would be required later.
Now, click on Settings.
From the blade, choose Keys from App Access.
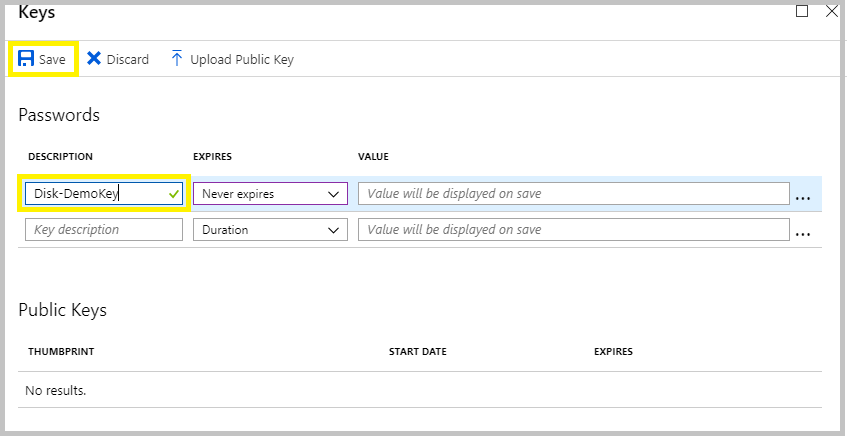
5. Enter the Key Description and Expiration time. Then Save the changes.
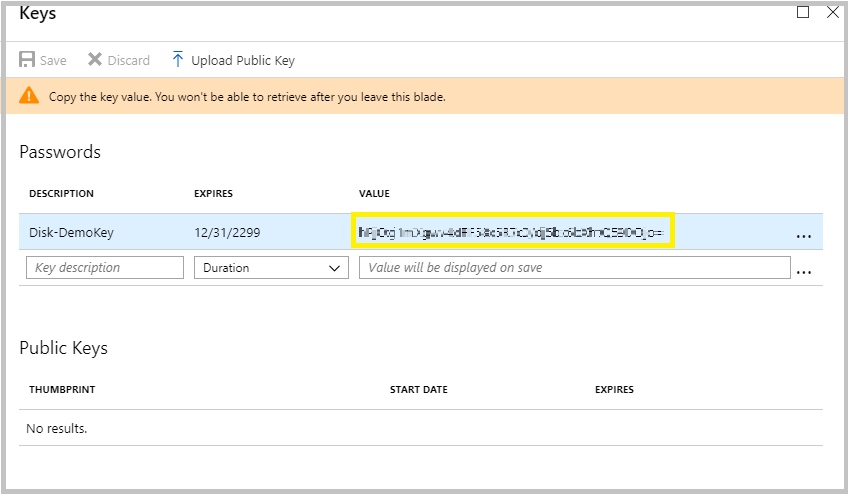
6. Before leaving the blade, copy the Key Valueas you won’t be able to retrieve after you leave this blade.
Create a cryptographic key for Azure Disk Encryption
1. In the portal, go to All Services and search for Azure Key Vaults.
2. Create a new Key Vault to save the Keys for the Encryption.
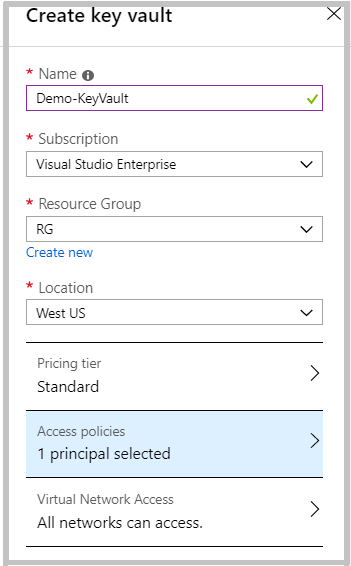
In the Access Policies, set the Key Permission for the encryption and click OK. Now, create the Key Vault.
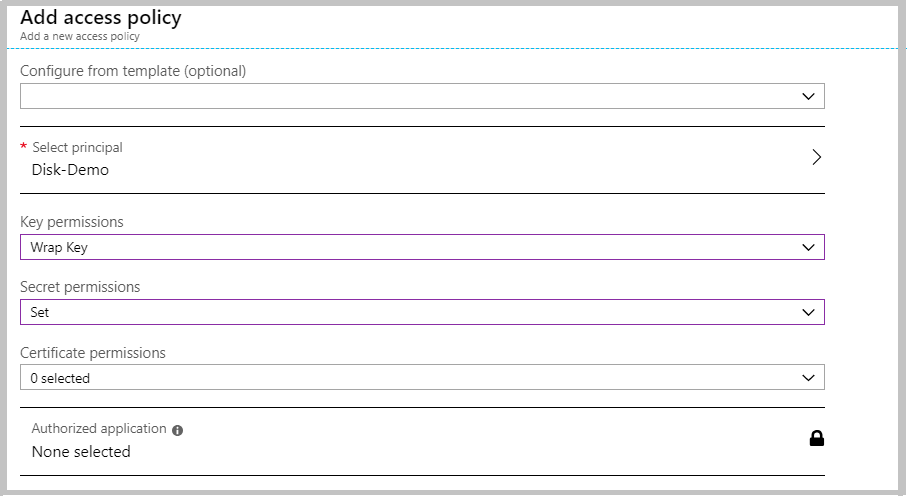
Note:
The WRAP operation is necessary for symmetric keys stored in Azure Key Vault since protection with an asymmetric key can be performed using the public portion of the key. This operation is supported for asymmetric keys as a convenience for callers that have a key-reference but do not have access to the public key material. This operation requires the keys/wrapKey permission.
The SET operation adds a secret to the Azure Key Vault. If the named secret already exists, Azure Key Vault creates a new version of that secret. This operation requires the secrets/set permission.
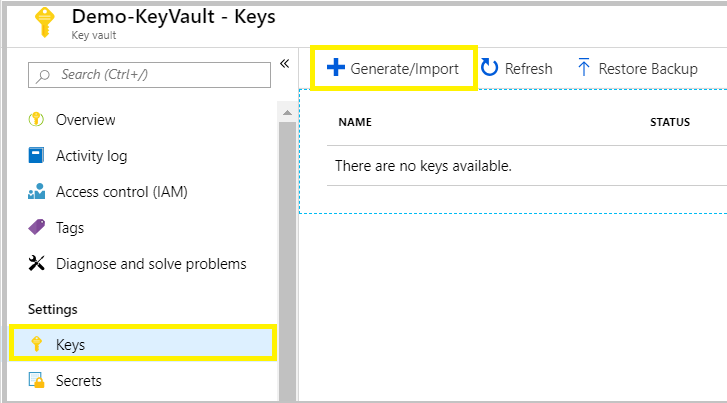
3. Once the Key Vault is created, go to the Key Vault. From the blade, under the Settings, choose Keys. Select +Generate/Import.
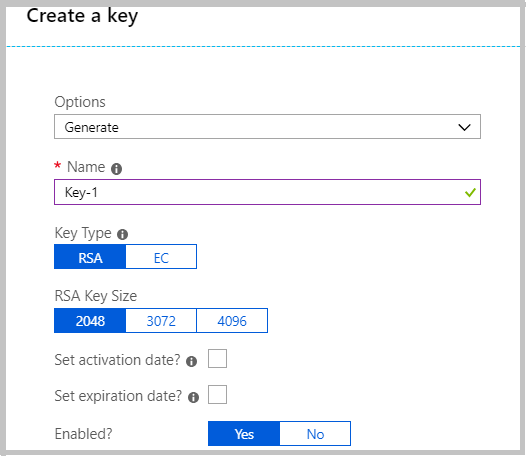
4. Enter the Key Name and Create the key.
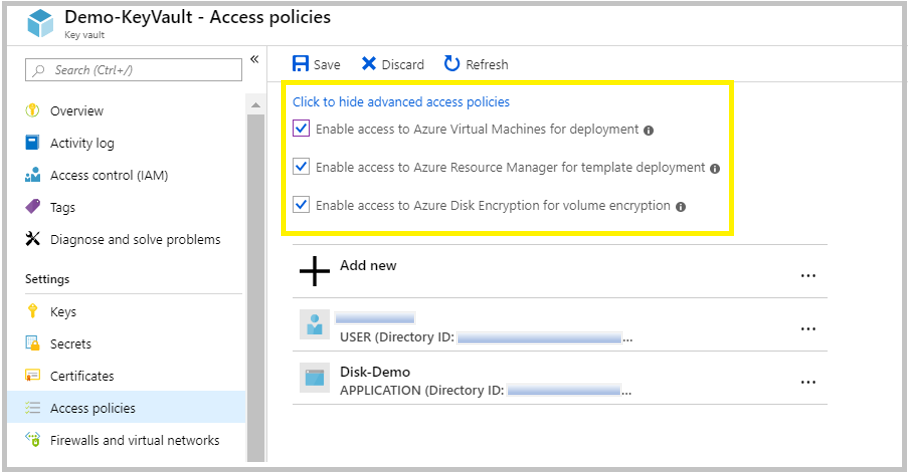
5. From the blade, under the Settings, go to Access Policies and Click to show advanced access policies. Enable the access options available there.
The Azure platform needs access to the encryption keys or secrets in your key vault to make them available to the VM for booting and decrypting the volumes. Enable disk encryption on the key vault or deployments will fail.
Enable encryption on existing or running IaaS Windows VMs
- Open the PowerShell and run the following script after checking the details in order to encrypt the disks.
2. Once the Script is run, go to the Azure Portal and check whether the disks are encrypted.
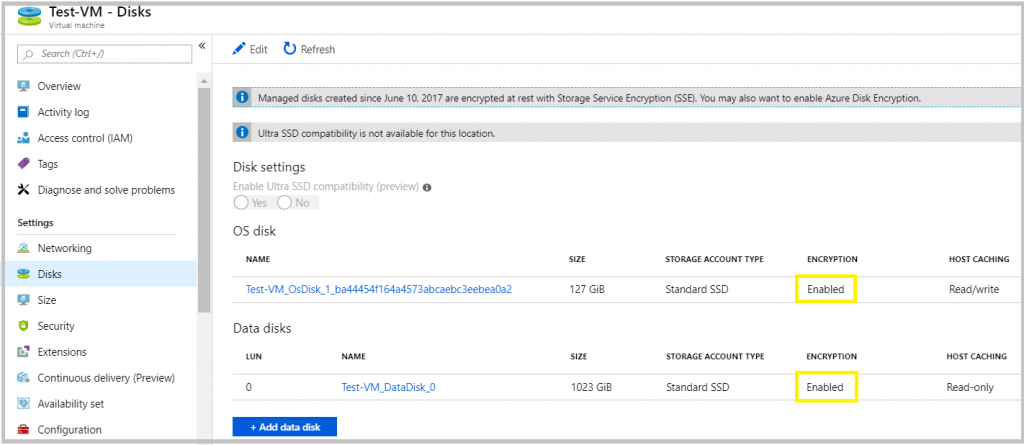
Disable encryption on existing or running IaaS Windows VMs
1. To Decrypt the Encryption use the following PowerShell script.
2. Once the Script is run, go to the Azure Portal and check whether the disks are encrypted.
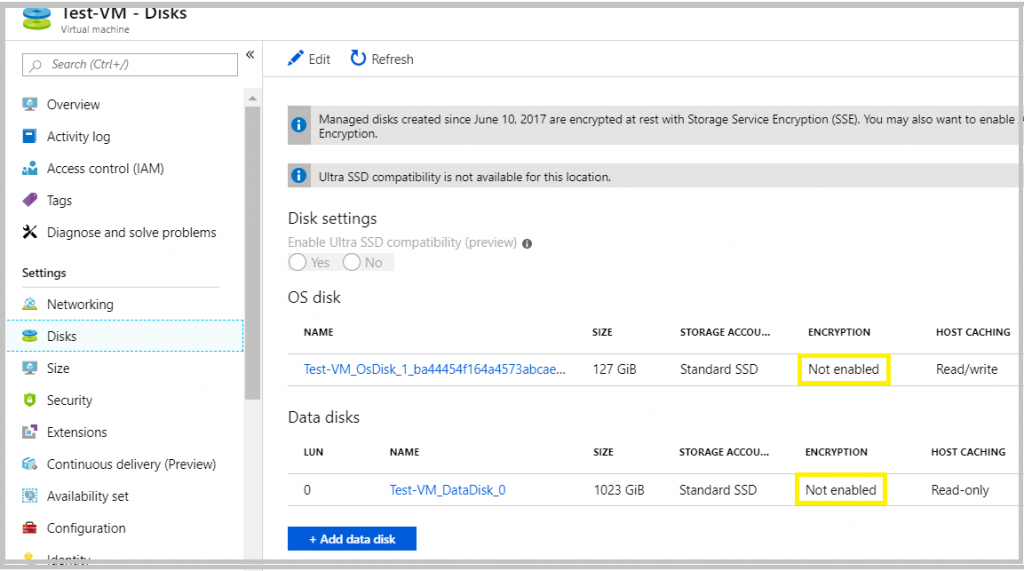
Interested in Microsoft Azure, Let’s CONNECT!











