Author – Rupesh Sonawane, Cloud Engineer
In today’s time creating and managing policies for different IT environments is important for staying compliant with your corporate standards. Azure Policy is one of the features provided by Azure that helps to enforce organizational standards and to assess compliance at scale, implementing governance for resource consistency, regulatory compliance, security, cost, and management.
It is challenging to manage a large number of policies among different environments and subscriptions granularly. Azure Blueprints can be one of the better solutions for this. But in many cases IT professionals ask for something that can give them more access to the code for these policies to see what Azure is cooking in the backend.
What if we provide a Policy-as-a-Code solution that will provide all the facilities from “Understanding the code of your Azure Policy definitions in detail” to “Updating your policies remotely and push them back to Azure”! Azure Policy as a Code with GitHub can make this possible for you something that Azure Blueprint cannot.
With this feature,
- You can easily export existing policies from the Azure portal and store them as files in the GitHub repository.
- You can collaborate in GitHub with other stakeholders to create or modify policy files.
- You can track all the changes that have been done and push all updates back to Azure using GitHub actions.
So let’s try this feature with a simple tutorial to see how it works!
Here, we are taking the scenario for policies on multiple subscriptions under your tenant.
Pre-requisites:
- The user must have an Owner role.
- User must have an Application Developer role for service principal creation.
- Subscriptions must be under one management group for scope selection.
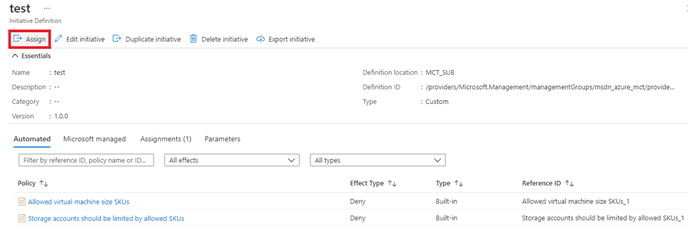
1. Creating Initiative Definition
The initiative definition is a logical grouping of Policy definitions that can be applied on a specific scope at one go.
- Log in to Azure Portal. On the search bar search Policy and click on the policy tab.
- Click on Definitions on the left pane.
- Click on Add Initiative Definition.
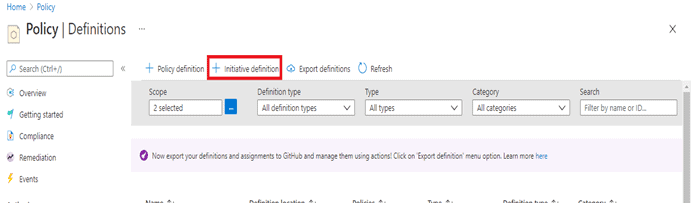
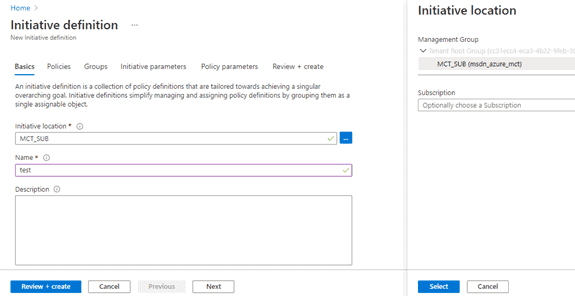
- To apply this on multiple subscriptions, put your all subscriptions under one management group and then select a scope as a management group of those subscriptions as shown below.
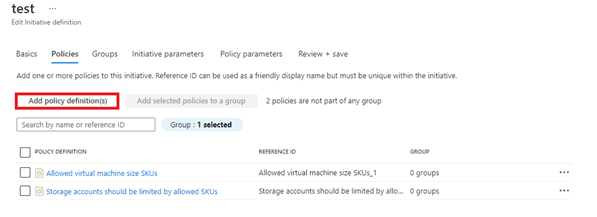
- On the Policies tab, click on add definitions and select multiple definitions to be applied on all subscriptions.
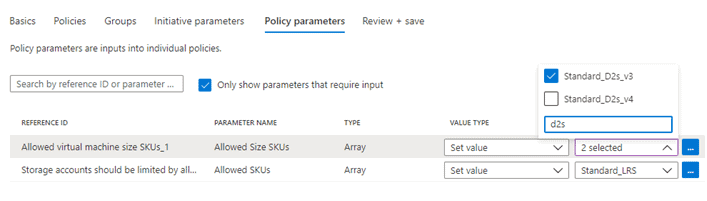
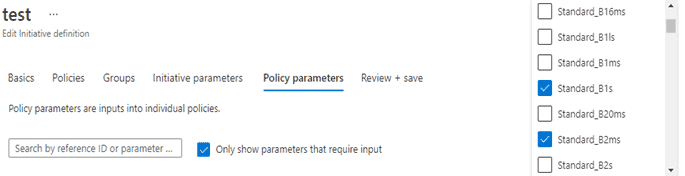
- On the Policy parameters tab, select values for selected definitions and create a policy initiative.
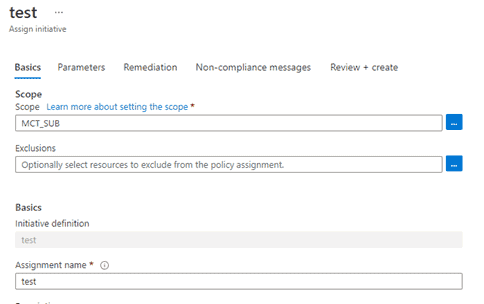
- After the creation of this initiative, it needs to be assigned to management scope. Click on Assign tab. Select a scope as a Management group and keep all things default. Click on create.
2. Exporting To GitHub
- On the basics, tab click on sign with GitHub and add your GitHub credentials. Select proper repository and branch to export your initiative.
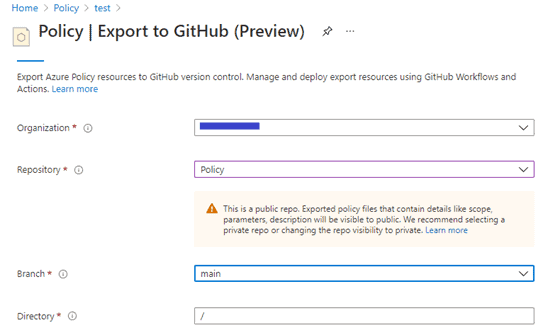
- On the Policies tab, select a scope as a management group, add an initiative definition if it does not come by default. Select Export options as Definition and Assignments. On the Assignments tab which might be showing “0 Assignments”, click on that and select your assigned initiative.
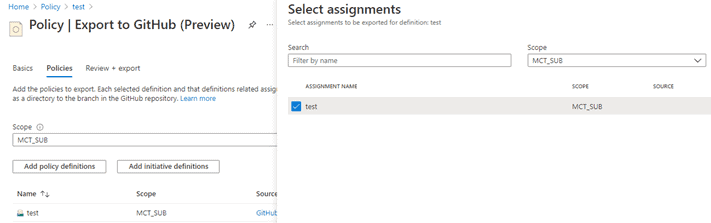
- Click on Review and Export.
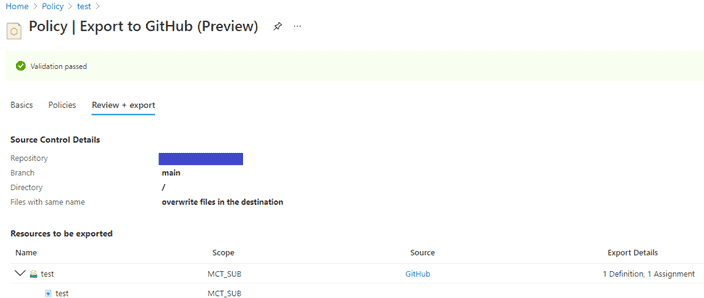
- In a given repository we can see initiative “test”.

- In the policyset.json file, we get all the JSON codes of the initiative that had been applied and exported.
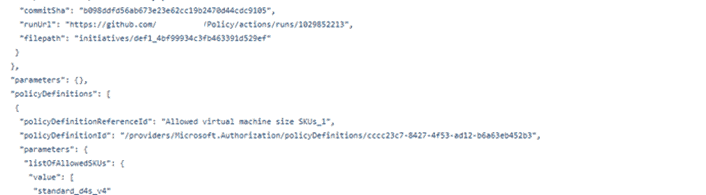
- In workflows, we can see the .yml file which shows the configurations Pushed from Azure.
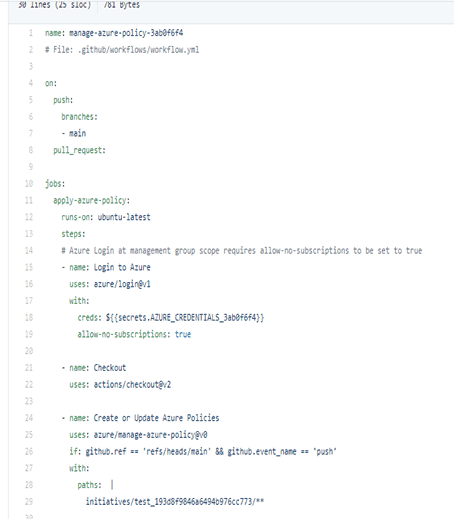
3. Updating the policy on GitHub and push the changes to Azure
Now from git Actions we can update this policy using Pull request and push it to Azure to update our policy initiative.
- Clone the repository from GitHub.
- We will make changes to the policyset.json file locally.
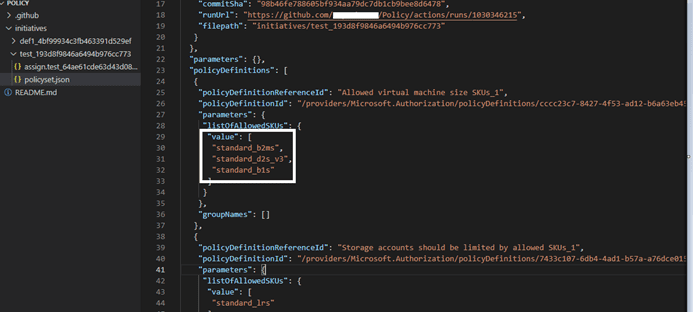
- Open file location in the code editor. Go to the policyset.json file and change the values as per requirements. Save the file.
- On the local system open Git bash at the file location and run the following commands to push changes to the repository locally. We are going to create a new branch here so that we can provide the necessary security approvals for pull requests.
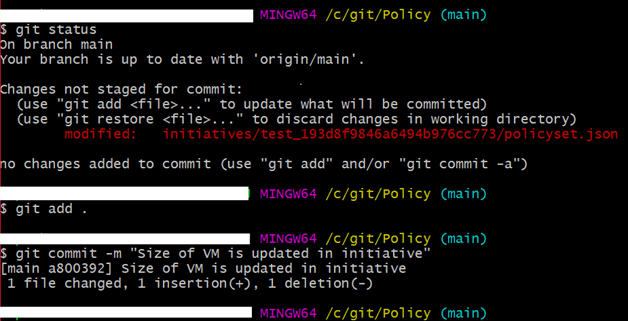
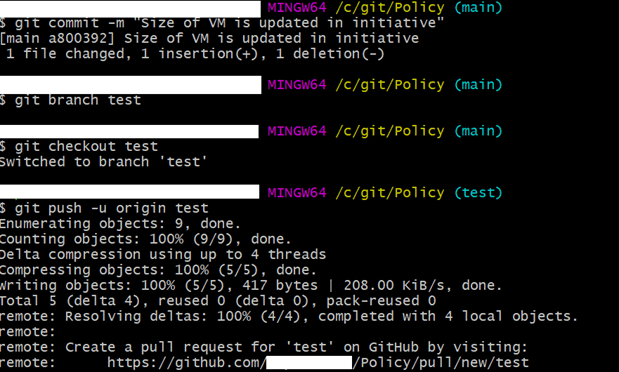
- Once it is done, we will get a prompt pull request on GitHub.
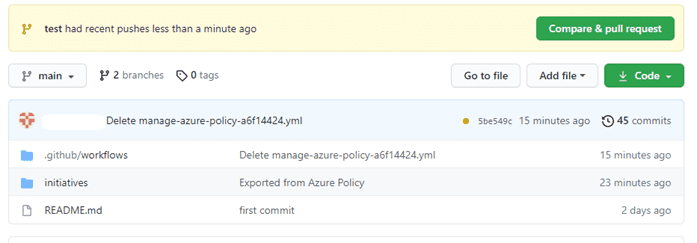
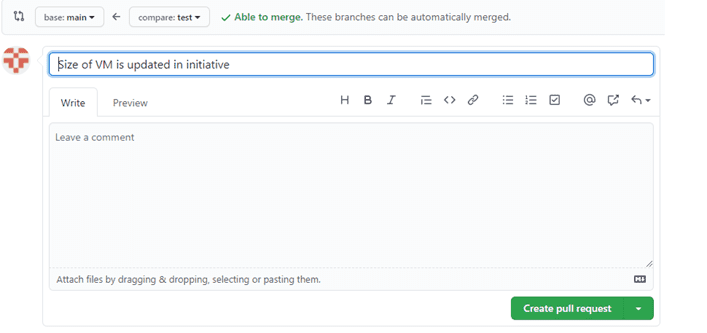
- Click On Compare and pull request and in the next window click on Create pull request.This will send an approval request to the branch owner of the repository. Once it’s approved, given changes will get stored in GitHub.
- Here we can see that the “Create or Update Azure Policies” tab is skipped; since we don’t have approval from the repository owner.
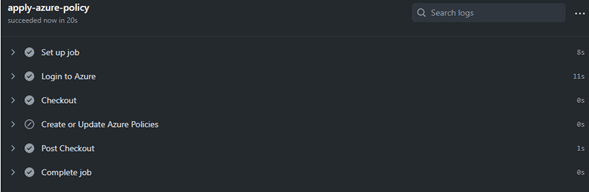
- Approval request to branch owner of the repository is being executed.
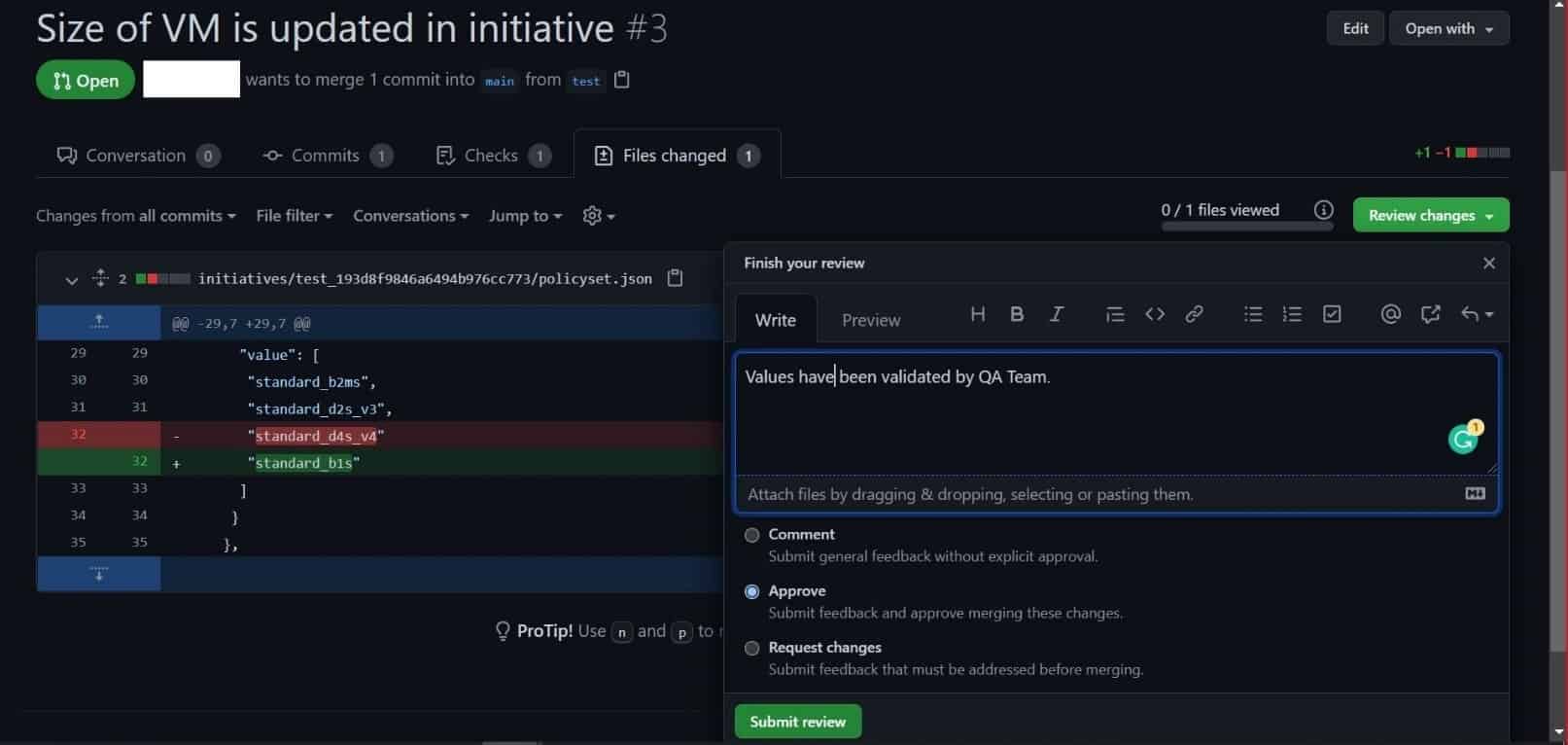
- Click On Merge Pull request.
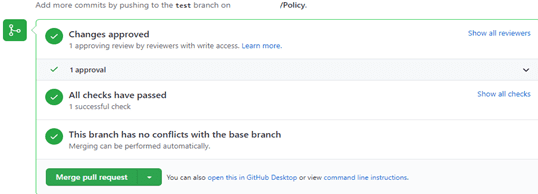
- As the condition has been set in the GitHub pipeline for updating and assigning, the policy action will only be triggered after a successful merging operation to be performed on the main branch. We can see the results in detail when we click on running workflow.

- We can verify the changes updated on Azure.
For additional reference, check the documentation.